Loop Security Controls
Security by Design
Isolation of Sensitive Data
Loop service focuses on the front-end customer engagement and experience portion of the client’s operations. As such Loop remains isolated from the client’s own highly sensitive data contained in its commercial and operations systems.
Loop in its default configuration hides entered customer contact information from associate users. It is not exposed to client users and not exposed via the Loop API. Collected contact information may only be used by Loop to facilitate a connection between Loop and the consumers (for example, to exchange messages and bring closure to the consumer’s input or request).
Privacy Policy:
In full production subscriptions, Loop can display a link to Benbria’s privacy policy or a link to the client’s own privacy policy.
The client’s Loop users are required to provide proof of identity to access their assigned Loop user interface. User authentication requires both:
- Username: Unique usernames are enforced within each client’s account.
- Password: Password is mandatory. The presentation of password is masked on the page during the authentication and password administration procedures. Passwords are stored in Loop in encrypted format; they are never retrievable in plain text.
Loop’s security reference design also specifies the following enhanced authentication capabilities:
- Enforcement of strong password rules, including a minimum character length and at least one alphabetic and one non-alphabetic character.
- Lockout following a prescribed number of invalid login attempts.
- Enforce periodic password change.
- Maintain user’s password history, preventing re-use.
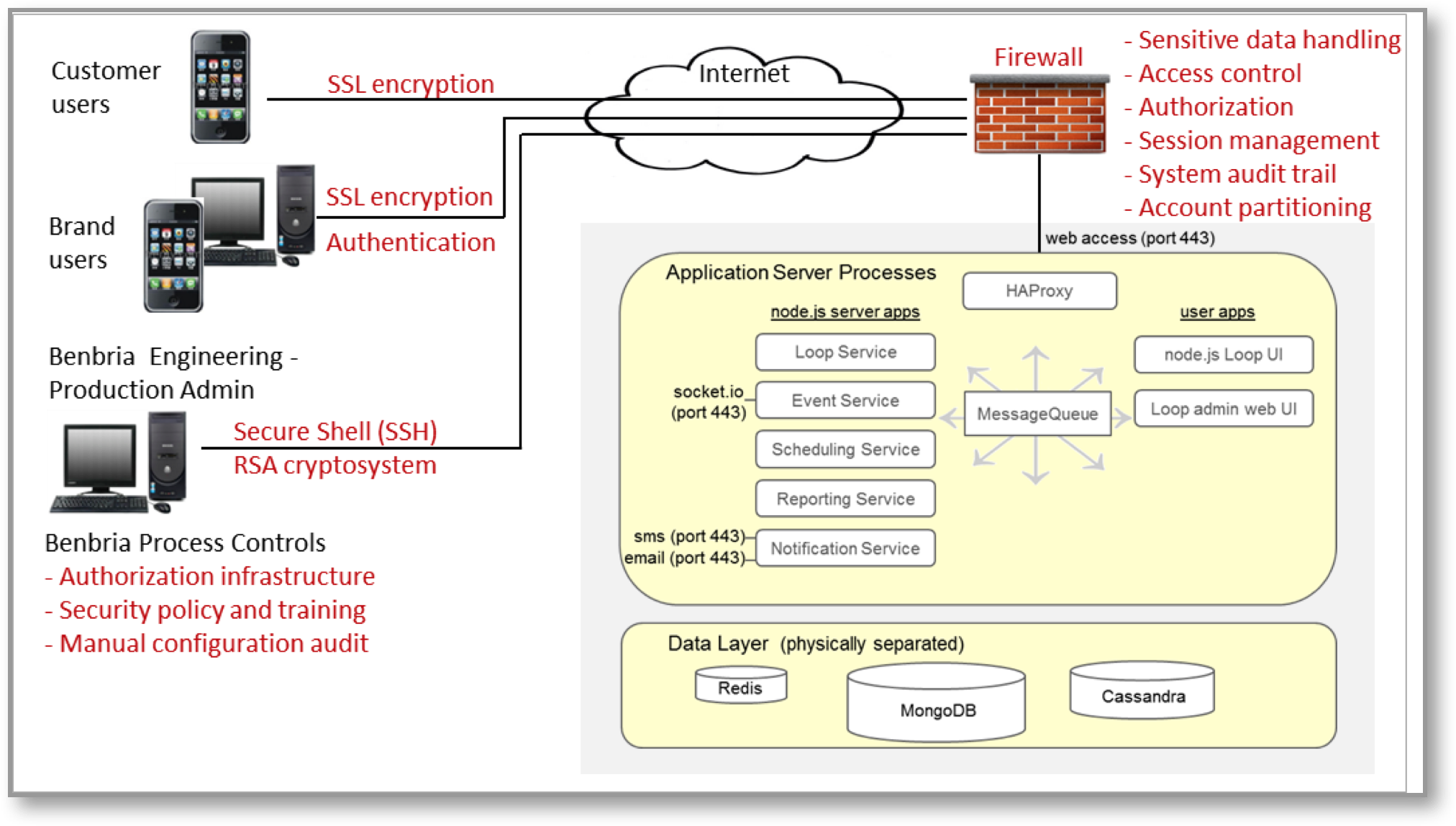
Reference Architecture
The following figure summarizes Loop’s security design reference, including key security measures in red text that is designed to keep data private and safe. Terminology is described in the sections that follow.

Component Layers and Overview
The figure below captures the components involved in managing data through the Loop platform, including the conceptual application layers (for reference):

Hosting Partners
Benbria works with two of the leading providers of cloud hosting services. As such, Benbria’s Loop product leverages best-in-class security from these hosts:
Consumer Rights
The client is obligated by applicable local, state/province, or national law to protect the privacy of customer information. Loop assists the client in meeting these legal obligations in the following ways:
- Hidden contact information: Loop in its default configuration hides entered customer contact information; it is not exposed to the client’s users and not exposed via its API. Collected contact information may only be used by the client to connect with customer users via Loop, for example to bring closure to the customer’s input or request.
- Privacy Policy: In full production subscriptions, Loop can display a link to Benbria’s privacy policy or a link to the client’s own privacy policy.
Physical Security
Physical Access
Physical controls are in place to prevent theft of customer data. Customer data is stored on best-in-class secure hosts (see Amazon, Terremark). Physical access to these datacenters is highly restricted.
Physical access to Benbria offices is protected by keycard access. Benbria offices are monitored 24/7 by a staffed security team.
In addition, the following physical security measures have been put in place in the hosting facility:
- Fire Detection and Suppression:
Automatic fire detection and suppression equipment has been installed to reduce risk.
- Power:
The data center electrical power systems are designed to be fully redundant and maintainable without impact to operations, 24 hours a day, and seven days a week. Uninterruptible Power Supply (UPS) units provide back-up power in the event of an electrical failure for critical and essential loads in the facility.
- Climate and Temperature:
Climate control is required to maintain a constant operating temperature for servers and other hardware, which prevents overheating and reduces the possibility of service outages.
- Management:
AWS monitors electrical, mechanical, and life support systems and equipment so that any issues are immediately identified. Preventative maintenance is performed to maintain the continued operability of equipment.
- Storage Device Decommissioning:
When a storage device has reached the end of its useful life, AWS procedures include a decommissioning process that is designed to prevent customer data from being exposed to unauthorized individuals. AWS uses the techniques detailed in DoD 5220.22-M (“National Industrial Security Program Operating Manual “) or NIST 800-88 (“Guidelines for Media Sanitization”) to destroy data as part of the decommissioning process. All decommissioned magnetic storage devices are degaussed and physically destroyed in accordance with industry-standard practices.
Online Access
Within the Benbria Engineering team, only the Development Operations (DevOps) team member, his alternate, his manager, and his director have the credentials to SSH to the hosted production environment.
Within the Benbria Operation/Support team, authenticated Ops team members have access to the Loop administrator’s UI, which has access to see account data and to modify account configuration. This access is required for deployment, operations, and support purposes.
No other Benbria members have access to the production environment.
Transmission Security
Data is encrypted during electronic transit when using the Internet and other unsecured networks. The connection between Benbria Engineering team members and the hosted Amazon or Terremark operating system is secured by the Secure Shell (SSH) cryptographic data protocol, including use of the RSA cryptosystem. The access is also enforced by strictly using Multi-Factor Authentication (MFA).
User Interface Security: The pipe between the hosted Loop application server and the user’s device is secured by the Secure Socket Layer (SSL) cryptographic protocol, where browsers and devices support it. SSL prevents data sent over the Internet from being retrieved; for example it prevents man-in-the-middle and phishing attacks.
Access points to the data are controlled by the authorization infrastructure of Benbria’s Loop product, which includes access control via username and strong password.
There is a user active session timeout provided by the SSH connection; socket session timeout occurs after approximately 10 minutes of detected inactivity. The loop application session timeouts are configurable.
Benbria utilizes many of the data and network security afforded by our hosting partner AWS.
- Secure Network Architecture:
Network devices, including firewall and other boundary devices, are in place to monitor and control communications at the external boundary of the network and at key internal boundaries within the network. These boundary devices employ rule sets, access control lists (ACL), and configurations to enforce the flow of information to specific information system services.
- Secure Access Points:
AWS has strategically placed a limited number of access points to the cloud to allow for a more comprehensive monitoring of inbound and outbound communications and network traffic.
- Distributed Denial Of Service (DDoS) Attacks.
AWS API endpoints are hosted on large, Internet-scale, world-class infrastructure that benefits from the same engineering expertise that has built Amazon into the world’s largest online retailer.
- Man in the Middle (MITM) Attacks.
All of the interactions with AWS APIs are done via SSL-protected endpoints, which provide server authentication.
- IP Spoofing.
Amazon EC2 instances cannot send spoofed network traffic. The AWS-controlled, host-based firewall infrastructure will not permit an instance to send traffic with a source IP or MAC address other than its own.
Data shall not be printed, exported or otherwise removed by Benbria staff.
Please see the “Loop Security Reference Architecture” (P3) summary table for more information.
Access Control
Policies and Management
Information security policies at Benbria are issued, approved, supported, and regularly reviewed by senior DevOps and engineers. The employees are informed of the best practices and security policies during security review meetings.
“Clear Desk” policy. Benbria’s IT Security Policy requires enabling session time-out settings on desktop and mobile devices. In addition, need-to-know data (e.g. for troubleshooting) shall not be printed.
Passwords & Authentication
A password policy is in place that included complexity, reuse, lockout and expiration. For administrative access to our accounts on Amazon and Terremark hosts: Amazon and Terremark security hardening features apply. Please see URL links (provided above) to Amazon and Terremark security documentation.
For client user access to the Loop Employee User Interface (our web UI): Loop supports complex passwords and third party policies for regular change as required.
Outsourcing
From time to time, subcontractors are used to provide service related to the delivery of Loop services. All security requirements are maintained in such cases.
User-Level Access Control
Loop provides a comprehensive authorization infrastructure that allows and constrains access and privileges to what is required for each user role. Role based authorization is applied automatically based on the user’s authentication information. The following sections and tables summarize the authorization structure of Loop in its default configuration:
Benbria Users and Employees
Loop’s authorization infrastructure (described above) applies also to Benbria personnel. Benbria carefully controls the number of employees that have access to the system and its account data. Most Benbria personnel have access to no more than loop data aggregated per market vertical. Only those authorized members of Benbria’s Engineering team whose role requires administering Production software deployments have access the to the hosted resources, the corresponding SSH private key, and account-specific data.
Benbria Authorized Users
|
Role:
|
Benbria Mgmt
& Loop Sales
|
Loop Engineers & Technical Support
|
Loop Engineer – Operations Admin
|
|
Access aggregate usage data
|
●
|
○
|
○
|
|
Access account configuration
|
●
|
●
|
●
|
|
Access UI-visible raw Loop data
|
|
●
|
●
|
|
Access customer contact data
|
|
●
|
●
|
|
Access user passwords
|
|
|
|
Notation: ● authorized by default for role, ○ authorization optionally available.
Similarly, Loop’s code development environment is access controlled. Only authorized Benbria Engineering team members have access to code repositories. And, an Authorization infrastructure ensures code is tightly configuration managed. For example:
- Development engineers create code and after internal review and peer approval through Pull Request process check-in to the Master Development branch of the code repository.
- The release engineer promotes version controlled code to a Candidate Release branch of the repository.
- Test engineers can perform functional testing on the deployed version of Candidate Release branch.
Other highlights of Benbria’s internal security policy include:
- Engineering team adherence to secure coding best practices.
- Security risk is documented and managed (i.e. threat risk assessments, vulnerability trees).
- Release management: each deployment is rigorously feature and regression tested on a separate staging server before deployment to production.
- Deployments to Production are full automated.
Client Users
The client’s users (staff or associates) are required to provide proof of identity to access their assigned Loop user interface. User authentication requires both:
- Username:
Unique usernames are enforced within each client’s account.
- Password:
Password is mandatory. The presentation of password is masked on the page during the authentication and password administration procedures. Passwords are stored in Loop in encrypted format; they are never retrievable in plain text.
The Loop security reference design also specifies the following enhanced authentication capabilities:
- Enforcement of strong password rules, including a minimum character length and at least one alphabetic and one non-alphabetic character.
-
Example permission configurations are provided below. Permissions can be defined per user:
|
Role:
|
Employee
|
Location
Manager
|
Group Manager
|
Area/Client
Manager
|
|
Loop inbox view
|
●
|
●
|
○
|
○
|
|
Loop internal note
|
○
|
●
|
○
|
|
|
Loop reassign
|
○
|
●
|
○
|
|
|
Loop response & close
|
○
|
●
|
○
|
|
|
Loop create on behalf
|
○
|
○
|
○
|
|
|
Loop escalate
|
|
○
|
○
|
|
|
Mobile Loop statistics
|
●
|
●
|
○
|
○
|
|
Location reports
|
|
●
|
●
|
○
|
|
Group reports
|
|
|
●
|
●
|
|
Area/Client reports
|
|
|
|
●
|
|
Administer my profile
|
●
|
●
|
●
|
●
|
Notation: ● authorized by default for role. ○ authorization optionally available.
Client Administrator Users
Administration rights can be granted to select Users, which enable the following:
|
Role:
|
Location Admin
|
Group Admin
|
Area/Client Admin
|
|
Administer employees
|
●
|
○
|
|
|
Administer location managers
|
●
|
○
|
|
|
Administer group managers
|
|
●
|
○
|
|
Administer area/client mgrs
|
|
|
●
|
|
Administer location events
|
●
|
|
|
|
Administer group events
|
|
●
|
|
|
Administer area/client events
|
|
|
●
|
|
Provision/configure locations
|
|
|
●
|
|
Configure system for client
|
|
|
●
|
|
Loop data system export
|
●
|
●
|
●
|
|
Administer system integration
|
●
|
○
|
●
|
|
Administer my profile
|
●
|
●
|
●
|
Notation: ● authorized by default for role. ○ authorization optionally available.
Notes:
- All authenticated users have access to modify their own personal information: username, password, name, organization, contact information, and contact preferences.
- Users of Loop’s core work flow are generally granted least privileges.
- A client member can be configured as both a client user and a client system administrator, of same organizational scope.
Consumer User
A consumer using Loop users can be categorized into one of the following:
- Anonymous:
Access Loop’s customer interface, provide the requested information, and choose not to enter any contact information.
- Contactable:
Complete the Loop workflow as described above, and choose to enter their contact information. For example, a customer may enter e-mail address or mobile phone number (for texting) so that the client can respond via Loop.
- Registered:
Registered customer users are configured and given a private link to access their personalized user interface. For example, the Hotel sends a private link to the Meeting Planner as part of an event welcome package.
Loop does not require consumer users to authenticate. As such, Loop treats all consumer users as external. Loop segregates consumer users from client users and client data. Consumer users can provide information into Loop, but the only data they have access to are automated and manually entered client comments.
|
Role:
|
Anonymous User
|
Contactable User
|
Registered User
|
|
Loop create
|
●
|
●
|
●
|
|
Loop dialog
|
○
|
●
|
●
|
|
Loop list
|
○
|
○
|
●
|
|
Personalized UI
|
|
|
●
|
|
Administer my contact info
|
|
●
|
●
|
|
Administer my profile
|
|
|
●
|
Notation: ● authorized by default for role. ○ authorization optionally available.